Highlights
Teiid Designer 8.6 introduces the following changes and features
- Support for a Native Query Procedure (TEIIDDES-1884)
- REST Importer Enhancements ( TEIIDDES-1829TEIIDDES-2190TEIIDDES-1882 )
- Added Dynamic Parameter Capability to REST Importer
- Added Dynamic Parameters to Generated REST Procedure
- Added JSON REST Web Service Support
- Improved Security Definition for Data Roles ( TEIIDDES-2274 )
- Numerous bug fixes
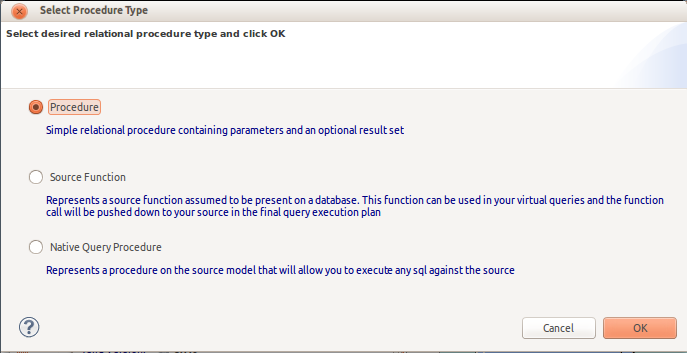
Support for Native Query Proceure
In Teiid Designer 8.6, we added support for a new source procedure type as shown below:
The resulting Create Relational Native Query Procedure dialog defaults to the following procedure structure:
- 0 or more input parameters (defined by the user)
- Result set with a single output column with object data type (user can edit/change the column name)
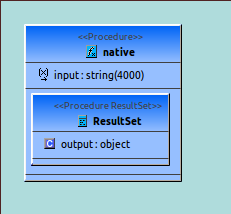
A sample procedure is shown below
REST Importer Enhancements
Added Dynamic Parameter Capability to REST Importer
Added Dynamic Parameters to Generated REST Procedure
Added JSON REST Web Service Support
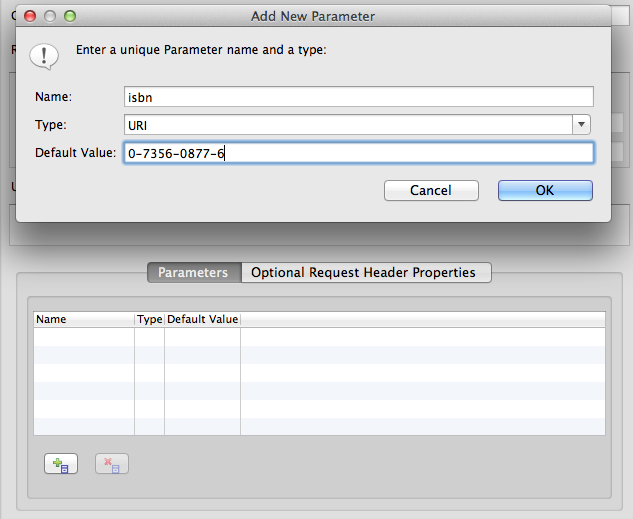
We have added dynamic parameters to the REST importer for cases where REST services do not have a static URL. The REST Connection Profile editor now has a tab to define dynamic parameters to be used in the generated procedure.
These parameters are then added to the generated virtual procedure in the transformation used for consuming the service.
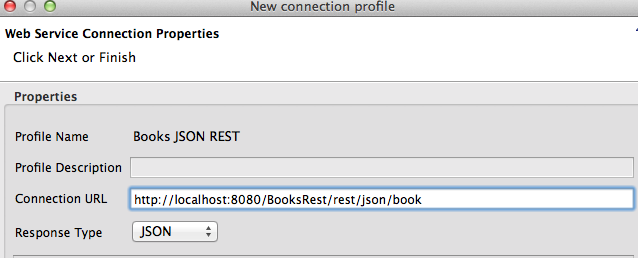
We also added support for generating transformations based on JSON REST Web Service sources. In the REST connection profile, there is a field to indicate whether the response type is JSON or XML.
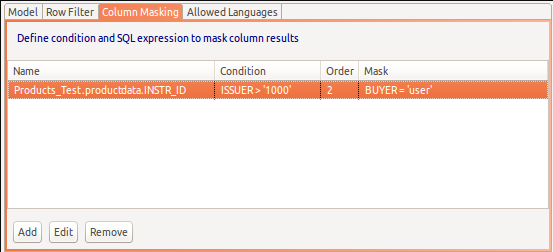
Improved Security Definition for Data Roles
In Teiid Designer 8.6, we cleaned up the UI support for defining and editing Row and Column Based Security as defined by Teiid's permission definition: Teiid 8.8 Reference Guide
Teiid provides 2 security concepts
- Row-Based Security is "a permission against a fully qualified table/view/procedure may also specify a condition."
- "Unlike the allow CRUD actions defined above, a condition is always applied - not just at the user query level. The condition can be any valid SQL referencing the columns of the table/view/procedure. Procedure result set columns may be referenced as proc.col. The condition will act as a row-based filter and as a checked constraint for insert/update operations."
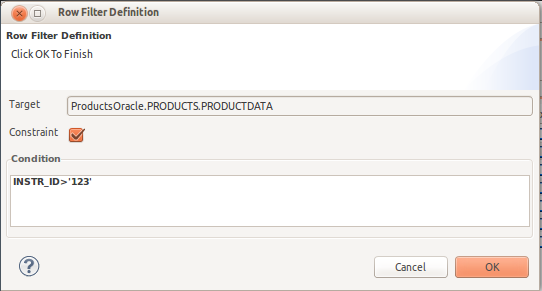
- An example of a condition might be:
column1=user()
- Column Masking is "a permission against a fully qualified table/view/procedure column may also specify a mask and optionally a condition."
- "When the query is submitted the roles are consulted and the relevant mask/condition information are combined to form a searched case expression to mask the values that would have been returned by the access. Unlike the CRUD allow actions defined above, the resulting masking effect is always applied - not just at the user query level. The condition and expression can be any valid SQL referencing the columns of the table/view/procedure. Procedure result set columns may be referenced as proc.col."
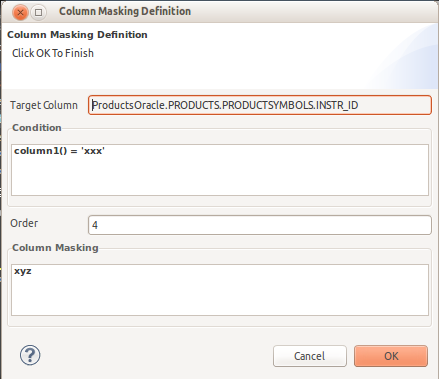
- An example of a mask might be: CASE WHEN column1=user() THEN column1 END
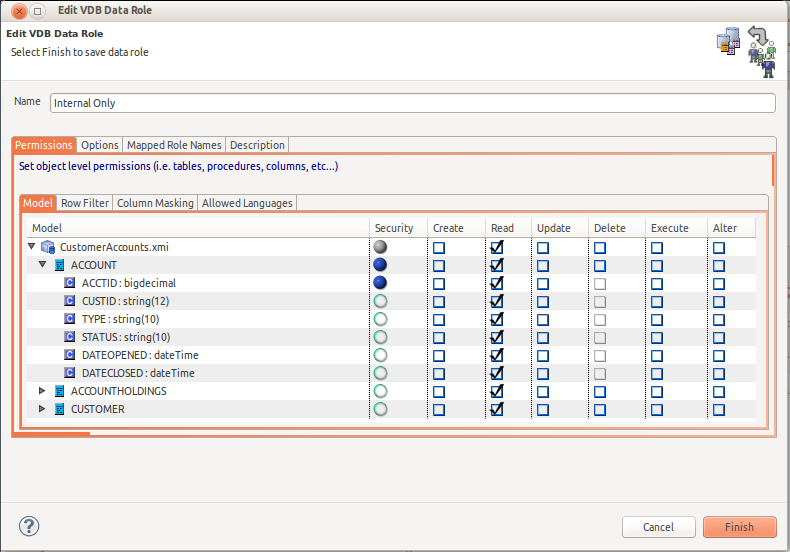
You can define Row and Column Based security in Designer's Data Row Wizard. By double-clicking a target table, view, procedure or column in the Models table, the appropriate editor dialog will be displayed. Not those objects that already have existing security defined are highlighted in blue.
If a table, view or procedure is double-clicked, the Row Filter Definition dialog is displayed. Enter a valid SQL condition and specify whether or not this filter should be treated as a constraint or not.
If a column is double-clicked, the Row Filter Definition dialog is displayed. Enter valid column masking SQL expression, an optional order (see Teiid documentation) and an option condition expression.
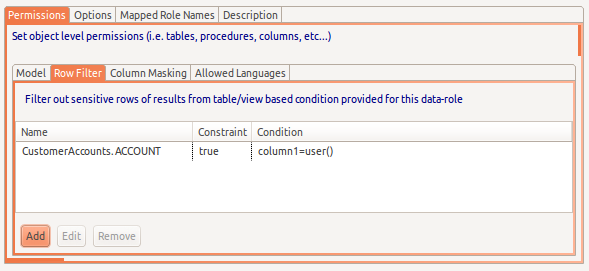
You can also edit these these values via the Add, Edit and Remove buttons on the respective Row Filter and Column Masking tabs
Comments