KeyCloak, Errai and bearer Token
victor.soria Dec 30, 2014 2:05 AMHi all,
The English is not my native language, but will try to make myself understood.
I'm building an application that uses Errai 3.1.0 for the view(modification of "Errai Security Demo"), Dropwizard for the rest backend (using the new Keycloak 1.1.0-Final Jetty 9.2.x Adapter) and Keycloak 1.1.0 Final appliance.
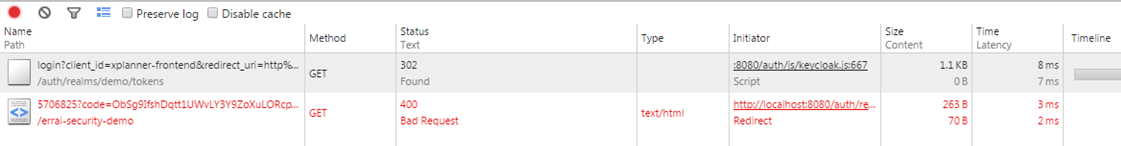
Everything was happiness until trying to make a REST call with security active in the backend(works fine without security adapter), Then I discovered that I had to enable CORS not only in dropwizard filters, Keycloak also needed to activate CORS.
I see keycloak/examples/cors at master · keycloak/keycloak · GitHub project and proceeded to set equivalent on my own project, i needed a obtain a bearer token in errai client and send Authentication header "Authentication: Bearer %#$%#$%$#%#$" to my dropwizard backend.
In the angular.js example (github link) they use interceptor:
module.factory('authInterceptor', function($q, Auth) {
return {
request: function (config) {
var deferred = $q.defer();
if (Auth.authz.token) {
Auth.authz.updateToken(5).success(function() {
config.headers = config.headers || {};
config.headers.Authorization = 'Bearer ' + Auth.authz.token;
deferred.resolve(config);
}).error(function() {
deferred.reject('Failed to refresh token');
});
}
return deferred.promise;
}
};
});
In my Errai code:
@Override
public void aroundInvoke(final RestCallContext context) {
RequestBuilder builder = context.getRequestBuilder();
builder.setHeader("Authorization", "Bearer eyJhbGciOiJSUzI1NiJ9...kHCIEIoqNt1YAesBN8W6-8X4k");
context.proceed();
}
}
And its work's... i get the message "token has expired" (I capture a token that had already expired and hardcode this for test purposes).
i need the bearer token (in angular they use Auth.authz.updateToken(5)), it is possible to have this information Errai? if this is not possible, I would give some clue as to where I should play the code?
Regards.