API Management: Policies
eric.wittmann Oct 15, 2013 4:46 PMOverview
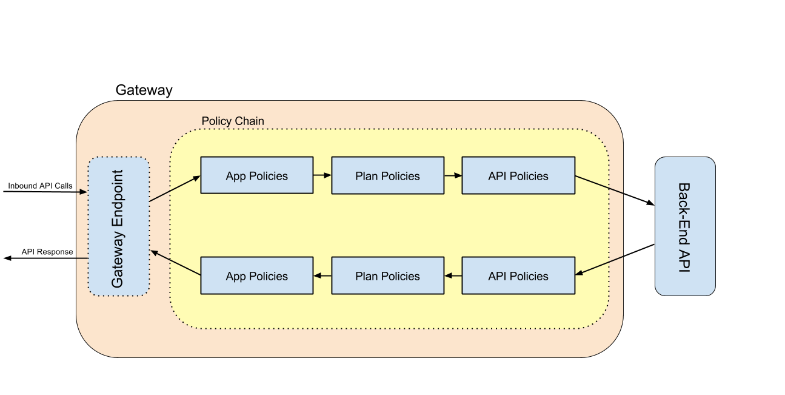
The real meat of the API Management Gateway is the concept of Policies. When the Gateway is satisfying an API request made by a client application, it first creates a Policy Chain for the request. The Policy Chain is a sequence of Policies that are executed. The policies are applied (in sequence) to the inbound request. Once the policies are applied, the inbound request is sent to the back end service implementation. The policies are then once again applied (in reverse sequence) to the response received from the back end service implementation.
Policies can be configured at the Application, Service, and Plan levels with the API Manager webapp. The order in which policies are applied as as follows:
- Receive Inbound Request from client application
- Apply Application Policies
- Apply Plan Policies
- Apply Service Policies
- Proxy Request to Back End
- Receive Response from Back End
- Apply Service Policies
- Apply Plan Policies
- Apply Application Policies
- Send Response to client application
Diagrams are always helpful!
What are Policies?
Policies implement all of the governance logic that we want to apply to an inbound request. Every Policy is an instance of a Policy Definition (which may built-in to the system or contributed by third parties). The Policy Definition includes meta-information about the Policy such as its type (access, metering, throttling, etc). The type is useful for categorizing policies and displaying them in the user interface (when managing services and applications) but is unimportant to the Gateway.
Here are some typical examples of Policies:
Access Policies - these types of policies control access to the Service. These policies could be configured to grant or deny access to the service based on authentication credentials included in the Request (e.g. BASIC authentication credentials passed in an HTTP Authorization header). They may be configured in various ways, for example to leverage existing sources of identity such as an LDAP directory. Here are some examples of Access Policies:
- Pass-Through Authentication Policy
- BASIC Authentication Policy using LDAP as the source of identity
- BASIC Authentication Policy using a Database as the source of identity
- OpenId Authentication Policy
- Authorization Policy using Drools to grant/revoke access
- IP Whitelist/Blacklist Policy
Throttling/Metering Policies - these policies track aggregate statistics such as # of requests performed per unit of time, typically for the purpose of billing or throttling.
Metrics Policies - these policies track metrics for the purpose of reporting significant statistics to Service and Application owners.
Custom Policies - this is a generic class of policies to cover domain/business specific logic that should be applied.