Mapping LDAP Groups with picketlink(GateIn 3.6)
juro.kunec Jul 18, 2014 11:09 AMHey
I am struggling with mapping between my OpenLDAP and picketlink in gatein 3.6. I checked all tutorials that I found on the internet
GateIn with LDAP as a default user and group store
http://docs.exoplatform.com/public/index.jsp?topic=%2FPLF41%2FPLFAdminGuide.LDAP.html
LDAP integration - GateIn Portal 3.8 - Project Documentation Editor
I can get working mapping users from ldap to platform(gatein) but if I map the groups from ldap to platform. I cant get access for the users, who are in these groups
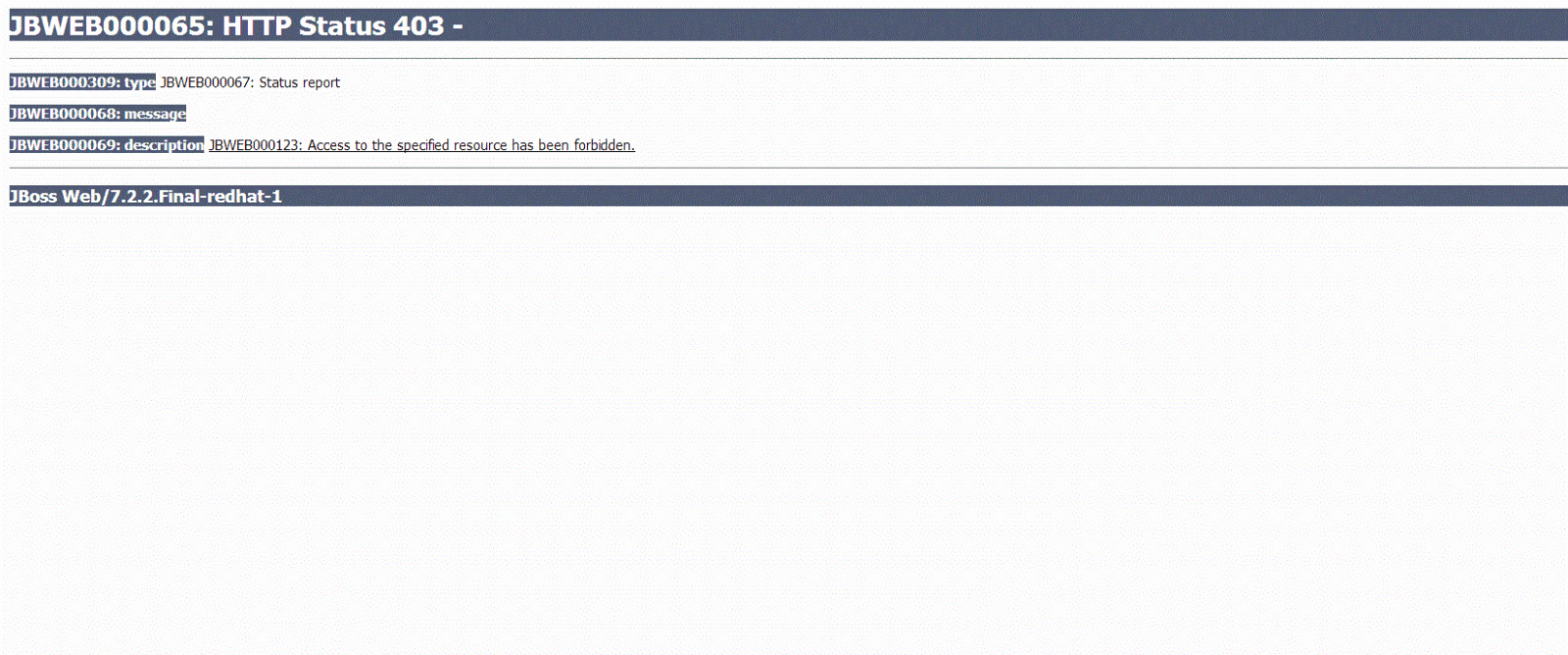
my output in browser
but if I uncomment these parts,where I map the groups in idm-configuration.xml and picketlink-idm-ldap-config.xml. excatly how it is done in tutorials
idm-configuration.xml
<?xml version="1.0" encoding="ISO-8859-1"?>
<!--
Copyright (C) 2009 eXo Platform SAS.
This is free software; you can redistribute it and/or modify it
under the terms of the GNU Lesser General Public License as
published by the Free Software Foundation; either version 2.1 of
the License, or (at your option) any later version.
This software is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
Lesser General Public License for more details.
You should have received a copy of the GNU Lesser General Public
License along with this software; if not, write to the Free
Software Foundation, Inc., 51 Franklin St, Fifth Floor, Boston, MA
02110-1301 USA, or see the FSF site: http://www.fsf.org.
-->
<configuration xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.exoplaform.org/xml/ns/kernel_1_2.xsd http://www.exoplaform.org/xml/ns/kernel_1_2.xsd"
xmlns="http://www.exoplaform.org/xml/ns/kernel_1_2.xsd">
<component>
<key>org.exoplatform.services.organization.idm.PicketLinkIDMCacheService</key>
<type>org.exoplatform.services.organization.idm.PicketLinkIDMCacheService</type>
</component>
<component>
<key>org.gatein.common.transaction.JTAUserTransactionLifecycleService</key>
<type>org.gatein.common.transaction.JTAUserTransactionLifecycleServiceImpl</type>
</component>
<component>
<key>org.exoplatform.services.database.HibernateService</key>
<jmx-name>database:type=HibernateService</jmx-name>
<type>org.exoplatform.services.organization.idm.CustomHibernateServiceImpl</type>
<init-params>
<properties-param>
<name>hibernate.properties</name>
<description>Default Hibernate Service</description>
<property name="hibernate.hbm2ddl.auto" value="update"/>
<property name="hibernate.show_sql" value="false"/>
<property name="hibernate.connection.datasource" value="${gatein.idm.datasource.name}${container.name.suffix}"/>
<property name="hibernate.connection.autocommit" value="false"/>
<!-- Non-JTA setup -->
<property name="hibernate.current_session_context_class" value="thread"/>
<!-- JTA setup -->
<!--<property name="hibernate.current_session_context_class" value="jta"/>
<property name="hibernate.transaction.factory_class" value="org.hibernate.transaction.JTATransactionFactory" />
<property name="hibernate.transaction.jta.platform" value="org.exoplatform.services.organization.idm.UserTransactionJtaPlatform" />-->
<property name="hibernate.cache.use_second_level_cache" value="false"/>
<property name="hibernate.cache.use_query_cache" value="false"/>
<!-- Uncomment for enable 2nd level cache based on Infinispan -->
<!--<property name="hibernate.cache.region.factory_class" value="org.jboss.as.jpa.hibernate4.infinispan.InfinispanRegionFactory" />-->
<!-- Uncomment to enable cache statistics for infinispan />-->
<!--<property name="hibernate.cache.infinispan.statistics" value="true" />-->
<!-- Uncomment to use custom infinispan configuration file instead of the default bundled in hibernate-infinispan jar -->
<!--<property name="hibernate.cache.infinispan.cfg" value="/home/infinispan/cacheprovider-configs.xml"/>-->
<!--
Should be automatically detected. Force otherwise
<property name="hibernate.dialect" value="org.hibernate.dialect.XXXDialect"/>
-->
<property name="hibernate.listeners.envers.autoRegister" value="false"/>
</properties-param>
</init-params>
</component>
<component>
<key>org.exoplatform.services.organization.idm.PicketLinkIDMService</key>
<type>org.exoplatform.services.organization.idm.PicketLinkIDMServiceImpl</type>
<init-params>
<value-param>
<name>config</name>
<!-- <value>war:/conf/organization/picketlink-idm/picketlink-idm-config.xml</value> -->
<!--Sample LDAP config-->
<value>file:${jboss.server.config.dir}/allianz/projectsuite/picketlink-idm-ldap-config.xml</value>
<!--Read Only "ACME" LDAP Example-->
<!--<value>war:/conf/organization/picketlink-idm/examples/picketlink-idm-ldap-acme-config.xml</value>-->
<!--OpenLDAP LDAP config-->
<!--<value>war:/conf/organization/picketlink-idm/examples/picketlink-idm-openldap-config.xml</value>-->
<!--OpenLDAP ReadOnly "ACME" LDAP Example-->
<!--<value>war:/conf/organization/picketlink-idm/examples/picketlink-idm-openldap-acme-config.xml</value>-->
<!--MSAD LDAP Example-->
<!--<value>war:/conf/organization/picketlink-idm/examples/picketlink-idm-msad-config.xml</value>-->
<!--MSAD Read Only "ACME" LDAP Example-->
<!--<value>war:/conf/organization/picketlink-idm/examples/picketlink-idm-msad-readonly-config.xml</value>-->
</value-param>
<!-- In default PicketLink IDM configuration hibernate store will namespace identity objects using this realm name
if you want to share DB between portal and also share the same identity data remove the "${container.name.suffix}" part-->
<value-param>
<name>portalRealm</name>
<value>idm_realm${container.name.suffix}</value>
</value-param>
<value-param>
<name>apiCacheConfig</name>
<value>war:/conf/organization/picketlink-idm/infinispan.xml</value>
</value-param>
<value-param profiles="cluster">
<name>apiCacheConfig</name>
<value>war:/conf/organization/picketlink-idm/infinispan-cluster.xml</value>
</value-param>
<value-param>
<name>storeCacheConfig</name>
<value>war:/conf/organization/picketlink-idm/infinispan.xml</value>
</value-param>
<value-param profiles="cluster">
<name>storeCacheConfig</name>
<value>war:/conf/organization/picketlink-idm/infinispan-cluster.xml</value>
</value-param>
<value-param>
<name>skipExpirationOfStructureCacheEntries</name>
<value>true</value>
</value-param>
<value-param>
<name>useSecureRandomService</name>
<value>true</value>
</value-param>
</init-params>
</component>
<component>
<key>org.exoplatform.services.organization.OrganizationService</key>
<type>org.exoplatform.services.organization.idm.PicketLinkIDMOrganizationServiceImpl</type>
<init-params>
<object-param>
<name>configuration</name>
<object type="org.exoplatform.services.organization.idm.Config">
<!-- For all ids not mapped with type in 'groupTypeMappings' use parent id path
as a group type to store group in PicketLink IDM. The effect of setting
this option to false and not providing any mappings under 'groupTypeMappings' option
is that there can be only one group with a given name in all GateIn group tree-->
<field name="useParentIdAsGroupType">
<boolean>true</boolean>
</field>
<!-- Group stored in PicketLink IDM with a type mapped in 'groupTypeMappings' will
automatically be member under mapped parent. Normally groups are linked by
PicketLink IDM group association - such relationship won't be needed then. It can
be set to false if all groups are added via GateIn APIs
This option may be useful with LDAP config as it will make (if set to true) every entry
added to LDAP (not via GateIn management UI) appear in GateIn-->
<field name="forceMembershipOfMappedTypes">
<boolean>true</boolean>
</field>
<!-- When 'userParentIdAsGroupType is set to true this value will be used to
replace all "/" chars in id. This is because "/" is not allowed to be
used in group type name in PicketLink IDM-->
<field name="pathSeparator">
<string>.</string>
</field>
<!-- Name of a group stored in PicketLink IDM that acts as root group in GateIn - "/" -->
<field name="rootGroupName">
<string>GTN_ROOT_GROUP</string>
</field>
<!-- Map groups added with GateIn API as a childs of a given group ID to be stored with a given
group type name in PicketLink IDM. If parent ID ends with "/*" then all child groups will
have the mapped group type. Otherwise only direct (first level) children will use this type.
This can be leveraged by LDAP setup. Given LDAP DN configured in PicketLink IDM to
store specific group type will then store one given branch in GateIn group tree while
all other groups will remain in DB. -->
<field name="groupTypeMappings">
<map type="java.util.HashMap">
<entry>
<key>
<string>/groups/*</string>
</key>
<value>
<string>group_type</string>
</value>
</entry>
<!-- Uncomment for sample LDAP configuration -->
<!-- <entry> -->
<!-- <key><string>/platform/*</string></key> -->
<!-- <value><string>platform_type</string></value> -->
<!-- </entry> -->
<!-- <entry> -->
<!-- <key><string>/organization/*</string></key> -->
<!-- <value><string>organization_type</string></value> -->
<!-- </entry> -->
<!-- Uncomment for ACME LDAP example -->
<!--
<entry>
<key><string>/acme/roles/*</string></key>
<value><string>acme_roles_type</string></value>
</entry>
<entry>
<key><string>/acme/organization_units/*</string></key>
<value><string>acme_ou_type</string></value>
</entry>
-->
<!-- Uncomment for MSAD ReadOnly LDAP example -->
<!--
<entry>
<key><string>/acme/roles/*</string></key>
<value><string>msad_roles_type</string></value>
</entry>
-->
</map>
</field>
<!-- If this option is used then each Membership created with MembrshipType that is
equal to value specified here will be stored in PicketLink IDM as simple
Group-User association-->
<field name="associationMembershipType">
<string>member</string>
</field>
<!-- if "associationMembershipType" option is used and this option is set to true
then Membership with MembershipType configured to be stored as PicketLink IDM association
will not be stored as PicketLink IDM Role in case that they are in groups from this parameter.
For RW LDAP setup, it's recommended to map all groups mapped to LDAP (all those from parameter groupTypeMappings)
However for DB only and/or Read-only LDAP, it's recommended to not map anything here -->
<field name="ignoreMappedMembershipTypeGroupList">
<collection type="java.util.ArrayList" item-type="java.lang.String">
<!-- Uncomment for sample LDAP config -->
<value>
<string>/groups/*</string>
</value>
</collection>
</field>
<!-- If 'true' will use JTA UserTransaction. If 'false' will use IDM transaction API -->
<field name="useJTA">
<boolean>false</boolean>
</field>
<!-- If PLIDM group will have name containing slash "/" char than it will be replace with following string.
Slashes are used in group paths and if present in names may cause unpredictable behaviour -->
<field name="slashReplacement">
<string>@_@_@</string>
</field>
<!-- If groups should be displayed in a sorted order in the management UI-->
<field name="sortGroups">
<boolean>true</boolean>
</field>
<!-- If memberships should be displayed in a sorted order in the management UI-->
<field name="sortMemberships">
<boolean>true</boolean>
</field>
<!-- For some LDAP configurations where part of users can duplicate in both DB and LDAP
it is not possible to count user efficiently for paginated query. Only way is to download
whole content of LDAP server and exclude duplicates manually to return accurate user count.
When this option is set to false GateIn will rely on user count information returned from PLIDM
which can return greater number of users then in real non duplicated count for perf reasons..
Those users will be filtered before returning search page however to not return nulls last entry
can be duplicated in returned user list.
If this value is set to true GateIn will perform whole non paginated query and filter it after.
It will result in more accurate results and paginated list size info however can affect performance
If you have DB only setup, it's recommended to switch this option to false. This will help to have better performance.
If you have DB+LDAP setup, it's recommended to switch this option to true, otherwise you can have inaccurate results -->
<field name="countPaginatedUsers">
<boolean>true</boolean>
</field>
<!-- For DB+LDAP it is not possible to efficiently perform paginated membership query. Only way is to download
all memberships from LDAP server and all memberships from DB and merge them together.
When this option is set to false GateIn will rely on membership count information returned from PLIDM
and it will use paginated membership queries based on this. This is better for performance but for DB+LDAP the
memberships pagination may not behave correctly.
If this value is set to true GateIn will perform whole non paginated query to obtain all memberships and filter it after.
It will result in more accurate results however can affect performance.
If you have DB only setup, it's recommended to switch this option to false. This will help to have better performance.
If you have DB+LDAP setup, it's recommended to switch this option to true, otherwise you can have inaccurate results -->
<field name="skipPaginationInMembershipQuery">
<boolean>true</boolean>
</field>
<!-- If true, the property lastLoginTime of user will be updated after successful authentication of this user to portal.
If false, the property won't be updated, which could have performance improvement in systems with many concurrent user logins -->
<field name="updateLastLoginTimeAfterAuthentication">
<boolean>false</boolean>
</field>
</object>
</object-param>
</init-params>
</component>
<external-component-plugins>
<target-component>org.exoplatform.services.naming.InitialContextInitializer</target-component>
<component-plugin>
<name>bind.datasource</name>
<set-method>addPlugin</set-method>
<type>org.exoplatform.services.naming.BindReferencePlugin</type>
<init-params>
<value-param>
<name>bind-name</name>
<value>${gatein.idm.datasource.name}${container.name.suffix}</value>
</value-param>
<value-param>
<name>class-name</name>
<value>javax.sql.DataSource</value>
</value-param>
<value-param>
<name>factory</name>
<value>org.apache.commons.dbcp.BasicDataSourceFactory</value>
</value-param>
<properties-param>
<name>ref-addresses</name>
<description>ref-addresses</description>
<property name="driverClassName" value="${portal.container.gatein.idm.datasource.driver}"/>
<property name="url" value="${portal.container.gatein.idm.datasource.url}"/>
<property name="username" value="${portal.container.gatein.idm.datasource.username}"/>
<property name="password" value="${portal.container.gatein.idm.datasource.password}"/>
</properties-param>
</init-params>
</component-plugin>
</external-component-plugins>
<external-component-plugins>
<target-component>org.exoplatform.services.database.HibernateService</target-component>
<component-plugin>
<name>add.hibernate.mapping</name>
<set-method>addPlugin</set-method>
<type>org.exoplatform.services.database.impl.AddHibernateMappingPlugin</type>
<init-params>
<values-param>
<name>hibernate.mapping</name>
<value>picketlink-idm/mappings/HibernateRealm.hbm.xml</value>
<value>picketlink-idm/mappings/HibernateIdentityObjectCredentialBinaryValue.hbm.xml</value>
<value>picketlink-idm/mappings/HibernateIdentityObjectAttributeBinaryValue.hbm.xml</value>
<value>picketlink-idm/mappings/HibernateIdentityObject.hbm.xml</value>
<value>picketlink-idm/mappings/HibernateIdentityObjectCredential.hbm.xml</value>
<value>picketlink-idm/mappings/HibernateIdentityObjectCredentialType.hbm.xml</value>
<value>picketlink-idm/mappings/HibernateIdentityObjectAttribute.hbm.xml</value>
<value>picketlink-idm/mappings/HibernateIdentityObjectType.hbm.xml</value>
<value>picketlink-idm/mappings/HibernateIdentityObjectRelationship.hbm.xml</value>
<value>picketlink-idm/mappings/HibernateIdentityObjectRelationshipType.hbm.xml</value>
<value>picketlink-idm/mappings/HibernateIdentityObjectRelationshipName.hbm.xml</value>
</values-param>
<values-param profiles="sybase">
<name>hibernate.mapping</name>
<value>picketlink-idm/sybase-mappings/HibernateRealm.hbm.xml</value>
<value>picketlink-idm/sybase-mappings/HibernateIdentityObjectCredentialBinaryValue.hbm.xml</value>
<value>picketlink-idm/sybase-mappings/HibernateIdentityObjectAttributeBinaryValue.hbm.xml</value>
<value>picketlink-idm/sybase-mappings/HibernateIdentityObject.hbm.xml</value>
<value>picketlink-idm/sybase-mappings/HibernateIdentityObjectCredential.hbm.xml</value>
<value>picketlink-idm/sybase-mappings/HibernateIdentityObjectCredentialType.hbm.xml</value>
<value>picketlink-idm/sybase-mappings/HibernateIdentityObjectAttribute.hbm.xml</value>
<value>picketlink-idm/sybase-mappings/HibernateIdentityObjectType.hbm.xml</value>
<value>picketlink-idm/sybase-mappings/HibernateIdentityObjectRelationship.hbm.xml</value>
<value>picketlink-idm/sybase-mappings/HibernateIdentityObjectRelationshipType.hbm.xml</value>
<value>picketlink-idm/sybase-mappings/HibernateIdentityObjectRelationshipName.hbm.xml</value>
</values-param>
</init-params>
</component-plugin>
</external-component-plugins>
</configuration>
picketlink-idm-ldap-config.xml
<?xml version="1.0" encoding="UTF-8"?> <!-- Copyright (C) 2009 eXo Platform SAS. This is free software; you can redistribute it and/or modify it under the terms of the GNU Lesser General Public License as published by the Free Software Foundation; either version 2.1 of the License, or (at your option) any later version. This software is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU Lesser General Public License for more details. You should have received a copy of the GNU Lesser General Public License along with this software; if not, write to the Free Software Foundation, Inc., 51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA, or see the FSF site: http://www.fsf.org. --> <jboss-identity xmlns="urn:picketlink:idm:config:v1_0_0_ga" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="urn:picketlink:idm:config:v1_0_0_ga identity-config.xsd"> <realms> <realm> <id>idm_realm_sample-portal</id> <repository-id-ref>DefaultPortalRepository</repository-id-ref> <identity-type-mappings> <user-mapping>USER</user-mapping> </identity-type-mappings> <options> <option> <name>cache.providerRegistryName</name> <value>apiCacheProvider</value> </option> <option> <name>credentialEncoder.class</name> <value>org.picketlink.idm.impl.credential.DatabaseReadingSaltEncoder</value> </option> <option> <name>credentialEncoder.hashAlgorithm</name> <value>SHA-256</value> </option> </options> </realm> <realm> <id>idm_realm</id> <repository-id-ref>PortalRepository</repository-id-ref> <identity-type-mappings> <user-mapping>USER</user-mapping> </identity-type-mappings> <options> <option> <name>template</name> <value>true</value> </option> <option> <name>cache.providerRegistryName</name> <value>apiCacheProvider</value> </option> <option> <name>credentialEncoder.class</name> <value>org.picketlink.idm.impl.credential.DatabaseReadingSaltEncoder</value> </option> <option> <name>credentialEncoder.hashAlgorithm</name> <value>SHA-256</value> </option> <option> <name>credentialEncoder.secureRandomAlgorithm</name> <value>SHA1PRNG</value> </option> </options> </realm> </realms> <repositories> <repository> <id>PortalRepository</id> <class>org.picketlink.idm.impl.repository.FallbackIdentityStoreRepository</class> <external-config /> <default-identity-store-id>HibernateStore</default-identity-store-id> <default-attribute-store-id>HibernateStore</default-attribute-store-id> <identity-store-mappings> <identity-store-mapping> <identity-store-id>PortalLDAPStore</identity-store-id> <identity-object-types> <identity-object-type>USER</identity-object-type> <identity-store-type>group_type</identity-store-type> </identity-object-types> <options /> </identity-store-mapping> </identity-store-mappings> <options> <option> <name>allowNotDefinedAttributes</name> <value>true</value> </option> </options> </repository> <repository> <id>DefaultPortalRepository</id> <class>org.picketlink.idm.impl.repository.WrapperIdentityStoreRepository</class> <external-config /> <default-identity-store-id>HibernateStore</default-identity-store-id> <default-attribute-store-id>HibernateStore</default-attribute-store-id> <!-- <identity-store-mappings> --> <!-- <identity-store-mapping> --> <!-- <identity-store-id>HibernateStore</identity-store-id> --> <!-- <identity-object-types> --> <!-- <identity-object-type>platform_type</identity-object-type> --> <!-- <identity-object-type>organization_type</identity-object-type> --> <!-- </identity-object-types> --> <!-- <options /> --> <!-- </identity-store-mapping> --> <!-- </identity-store-mappings> --> </repository> </repositories> <stores> <attribute-stores /> <identity-stores> <identity-store> <id>HibernateStore</id> <class>org.picketlink.idm.impl.store.hibernate.HibernateIdentityStoreImpl</class> <external-config /> <supported-relationship-types> <relationship-type>JBOSS_IDENTITY_MEMBERSHIP</relationship-type> <relationship-type>JBOSS_IDENTITY_ROLE</relationship-type> </supported-relationship-types> <supported-identity-object-types> <identity-object-type> <name>USER</name> <relationships /> <credentials> <credential-type>PASSWORD</credential-type> </credentials> <attributes /> <options /> </identity-object-type> </supported-identity-object-types> <options> <option> <name>hibernateSessionFactoryRegistryName</name> <value>hibernateSessionFactory</value> </option> <option> <name>populateRelationshipTypes</name> <value>true</value> </option> <option> <name>populateIdentityObjectTypes</name> <value>true</value> </option> <option> <name>allowNotDefinedIdentityObjectTypes</name> <value>true</value> </option> <option> <name>allowNotDefinedAttributes</name> <value>true</value> </option> <option> <name>allowNotCaseSensitiveSearch</name> <value>true</value> </option> <option> <name>isRealmAware</name> <value>true</value> </option> <option> <name>lazyStartOfHibernateTransaction</name> <value>true</value> </option> </options> </identity-store> <identity-store> <id>PortalLDAPStore</id> <class>org.picketlink.idm.impl.store.ldap.LDAPIdentityStoreImpl</class> <external-config /> <supported-relationship-types> <relationship-type>JBOSS_IDENTITY_MEMBERSHIP</relationship-type> </supported-relationship-types> <supported-identity-object-types> <identity-object-type> <name>USER</name> <relationships /> <credentials> <credential-type>PASSWORD</credential-type> </credentials> <attributes> <attribute> <name>firstName</name> <mapping>cn</mapping> <type>text</type> <isRequired>false</isRequired> <isMultivalued>false</isMultivalued> <isReadOnly>false</isReadOnly> </attribute> <attribute> <name>lastName</name> <mapping>sn</mapping> <type>text</type> <isRequired>false</isRequired> <isMultivalued>false</isMultivalued> <isReadOnly>false</isReadOnly> </attribute> <attribute> <name>email</name> <mapping>mail</mapping> <type>text</type> <isRequired>false</isRequired> <isMultivalued>false</isMultivalued> <isReadOnly>false</isReadOnly> <isUnique>false</isUnique> </attribute> </attributes> <options> <option> <name>idAttributeName</name> <value>cn</value> </option> <option> <name>passwordAttributeName</name> <value>userPassword</value> </option> <option> <name>ctxDNs</name> <value>ou=People,dc=maxcrc,dc=com</value> </option> <option> <name>allowCreateEntry</name> <value>true</value> </option> <option> <name>createEntryAttributeValues</name> <value>objectClass=Top</value> <value>objectClass=Person</value> <value>objectClass=organizationalPerson</value> <value>objectClass=inetOrgPerson</value> <!--value>objectClass=alatWebPortal</value--> <value>sn= </value> <value>cn= </value> </option> </options> </identity-object-type> <identity-object-type> <name>group_type</name> <relationships> <relationship> <relationship-type-ref>JBOSS_IDENTITY_MEMBERSHIP</relationship-type-ref> <identity-object-type-ref>USER</identity-object-type-ref> </relationship> <relationship> <relationship-type-ref>JBOSS_IDENTITY_MEMBERSHIP</relationship-type-ref> <identity-object-type-ref>group_type</identity-object-type-ref> </relationship> </relationships> <credentials/> <attributes/> <options> <option> <name>idAttributeName</name> <value>cn</value> </option> <option> <name>passwordAttributeName</name> <value>userPassword</value> </option> <option> <name>ctxDNs</name> <value>ou=Groups,dc=maxcrc,dc=com</value> </option> <option> <name>parentMembershipAttributeName</name> <value>member</value> </option> <option> <name>isParentMembershipAttributeDN</name> <value>true</value> </option> </options> </identity-object-type> </supported-identity-object-types> <options> <option> <name>providerURL</name> <value>ldap://127.0.0.1:389</value> </option> <option> <name>adminDN</name> <value>cn=Manager,dc=maxcrc,dc=com</value> </option> <!--option> <name>adminPath</name> <value>ou=WEB,o=CORE</value> </option --> <option> <name>adminPassword</name> <value>secret</value> </option> <option> <name>searchTimeLimit</name> <value>60000</value> </option> <option> <name>createMissingContexts</name> <value>false</value> </option> <option> <name>customJNDIConnectionParameters</name> <value>com.sun.jndi.ldap.connect.pool=true</value> </option> <option> <name>customSystemProperties</name> <value>com.sun.jndi.ldap.connect.pool.maxsize=300000</value> <value>com.sun.jndi.ldap.connect.pool.protocol=plain ssl</value> </option> <option> <name>cache.providerRegistryName</name> <value>storeCacheProvider</value> </option> <option> <name>allowNotCaseSensitiveSearch</name> <value>true</value> </option> </options> </identity-store> </identity-stores> </stores> <options> <option> <name>defaultTemplate</name> <value>idm_realm</value> </option> </options> </jboss-identity>
My OpenLDAP entry
version: 1 dn: dc=maxcrc,dc=com objectClass: top objectClass: domain dc: maxcrc dn: ou=Groups,dc=maxcrc,dc=com objectClass: top objectClass: organizationalUnit ou: Groups dn: cn=Man,ou=Groups,dc=maxcrc,dc=com objectClass: top objectClass: groupOfNames cn: Man member: cn=user1 dn: cn=Woman,ou=Groups,dc=maxcrc,dc=com objectClass: top objectClass: groupOfNames cn: Woman member: cn=user2 dn: ou=People,dc=maxcrc,dc=com objectClass: organizationalUnit objectClass: top ou: People description: Container for user entries dn: cn=user1,ou=People,dc=maxcrc,dc=com objectClass: top objectClass: person objectClass: organizationalPerson objectClass: inetOrgPerson cn: user1 sn: Mustemann mail: mustermann@gmail.com userPassword:: dGVzdA== dn: cn=user2,ou=People,dc=maxcrc,dc=com objectClass: top objectClass: person objectClass: organizationalPerson objectClass: inetOrgPerson cn: user2 sn: Musterfrau mail: musterfrau@gmail.com userPassword:: dGVzdA==
My goal is to read groups from ldap via API. I dont know how i can use Organization API. for example GroupHandler oder UserHandler with Picketlink IDM. I wanna to enable some portlets just for some groups of users.