-
1. Re: Readonly Auditor Role
mchoma Aug 1, 2018 9:08 AM (in response to pmm)In jira you mentioned (JBEAP-13845), there is in workaround section written Monitor role should be enough. Could you have a try?
-
2. Re: Readonly Auditor Role
pmm Aug 1, 2018 3:35 PM (in response to mchoma)mchoma wrote:
In jira you mentioned (JBEAP-13845), there is in workaround section written Monitor role should be enough. Could you have a try?
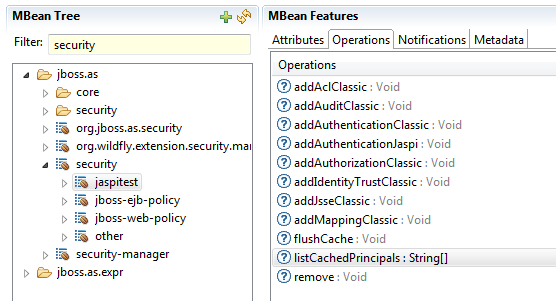
The Monitor role is not enough, if I assign the Monitor role the mbeans for the security domains ("jaspitest", "jboss-ejb-policy", "jboss-web-policy", "other") under the "security" mbean will not be visible.
-
3. Re: Readonly Auditor Role
mchoma Aug 2, 2018 11:52 AM (in response to pmm)So what about tweak RBAC to let you call security domain jmx?
E.g. does this makes it visible for Monitore role?
/core-service=management/access=authorization/constraint=sensitivity-classification/type=security/classification=security-domain:write-attribute(name=requires-addressable,value=false)
/core-service=management/access=authorization/constraint=sensitivity-classification/type=core/classification=security-domain:write-attribute(name=requires-addressable,value=false)
Because security-domain is defined as
"access-constraints" => { "sensitive" => {"security-domain" => {"type" => "core"}}, "application" => {"security-domain" => {"type" => "security"}} }, -
4. Re: Readonly Auditor Role
pmm Aug 3, 2018 7:51 AM (in response to mchoma)mchoma wrote:
So what about tweak RBAC to let you call security domain jmx?
E.g. does this makes it visible for Monitore role?
/core-service=management/access=authorization/constraint=sensitivity-classification/type=security/classification=security-domain:write-attribute(name=requires-addressable,value=false)
/core-service=management/access=authorization/constraint=sensitivity-classification/type=core/classification=security-domain:write-attribute(name=requires-addressable,value=false)
Because security-domain is defined as
"access-constraints" => { "sensitive" => {"security-domain" => {"type" => "core"}}, "application" => {"security-domain" => {"type" => "security"}} }, I get the following error message
$/core-service=management/access=authorization/constraint=sensitivity-classification/type=security/classification=security-domain:write-attribute(name=requires-addressable,value=false)
{
"outcome" => "failed",
"failure-description" => "WFLYCTL0201: Unknown attribute 'requires-addressable'",
"rolled-back" => true
}
$/core-service=management/access=authorization/constraint=sensitivity-classification/type=core/classification=security-domain:write-attribute(name=requires-addressable,value=false)
{
"outcome" => "failed",
"failure-description" => "WFLYCTL0201: Unknown attribute 'requires-addressable'",
"rolled-back" => true
}